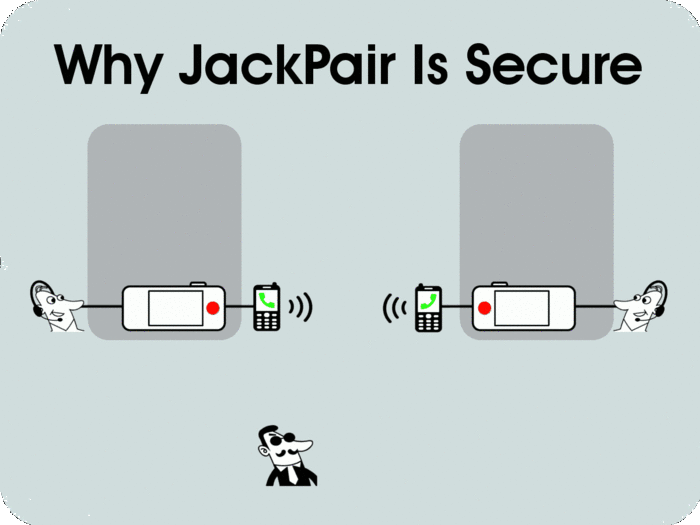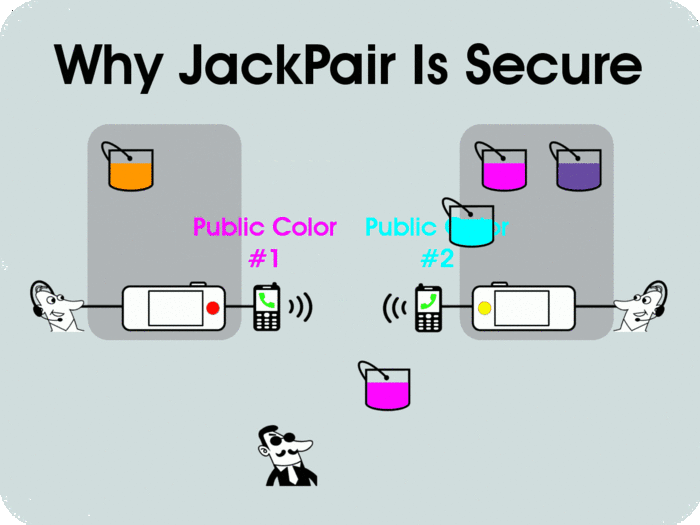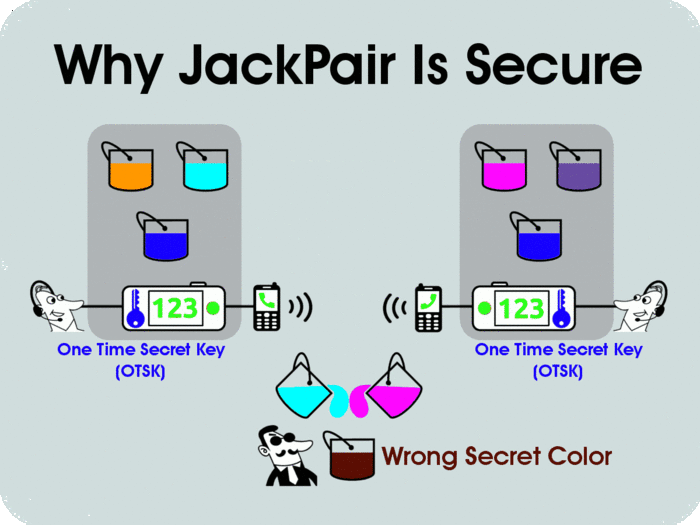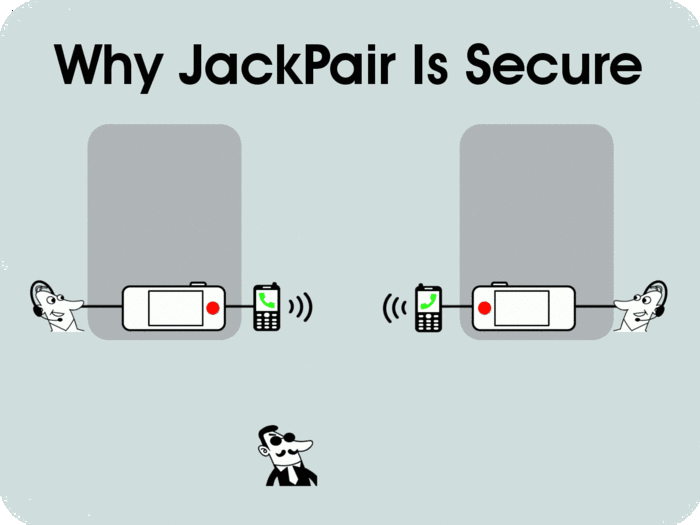
At any time during your phone call, when you push the JackPair button, a new One-Time-Secret-Key (OTSK) is generated to encrypt your voice conversation. This OTSK is created locally in each of the JackPair devices at both ends of the phone call without being exposed over the network(*), and it is destroyed immediately after the phone call is finished, without being stored anywhere outside the JackPair device. The OTSK is short-lived and self-managed; it never leaves the JackPair box. So there is no chance for the OTSK to be compromised by anybody, whether intentionally or accidentally. This simple security design leaves no trace behind; it not only protects your voice, but also saves us, as the device maker, from the trouble of being harassed by the government or exploited by hackers. Besides key exchange protocols, the encryption algorithm in JackPair is based on Salsa20 stream cipher, which is selected by eSTREAM, the ENCRYPT Stream Cipher Project organized by the European Union, as part of its final software portfolio since 2008. Stream Cipher like Salsa20 is a natural fit with OTSK, which is used as the seed for PRNG (Pseudo Randon Number Generator) to create key streams with similar property of One-Time Pad. JackPair uses open source encryption software and will stay open sourced. (*): The One-Time-Secret-Key in JackPair is generated using Diffie-Hellman-Merkle key exchange protocol, which is a well-known, fundamental protocol in the security industry since 1976; it allows creation of shared secret without exchanging it over the network (see illustration below).
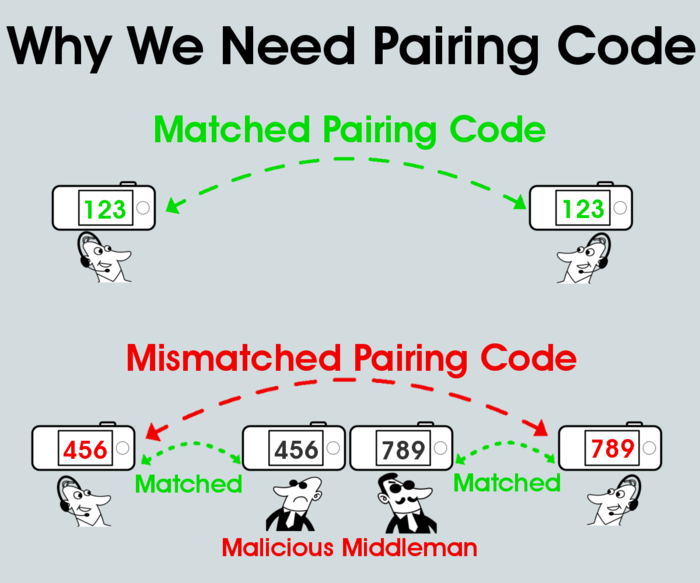
JackPair is designed with end-to-end security in mind: there’s no relay server or service provider involved in either the voice encryption or the One-Time-Secret-Key (OTSK) creation, and the OTSK is never disclosed anywhere, not even to the other party on the phone call. In order to make sure both sides use the same OTSK for voice encryption and there’s no middleman bridging the call, the Pairing Code(*) is designed as a simple way for both parties to authenticate each other through their own voices over the same phone phone. After your JackPair device has paired up with the other party’s (ie, when the LED light turns from red to green), The first thing you should do is to read the Pairing Code on your screen to the other party over the phone, and verify that the Pairing Code is the same on both ends. The fact that the other party recognizes your voice and acknowledges with the same Pairing Code means these two JackPair devices are directly connecting with each other, with no middleman bridging the call through any other JackPair devices. (*): Pairing Code is the abbreviated hash digest number of One-Time-Secret-Key (OTSK).